IP Camera Security Risks On Telegram: What You Need To Know
Is the allure of readily accessible, live surveillance footage a siren song luring users into a dangerous digital realm? The proliferation of hacked IP cameras and the channels on platforms like Telegram dedicated to sharing their illicit feeds presents a significant threat to privacy and security, exposing individuals to potential exploitation and harm.
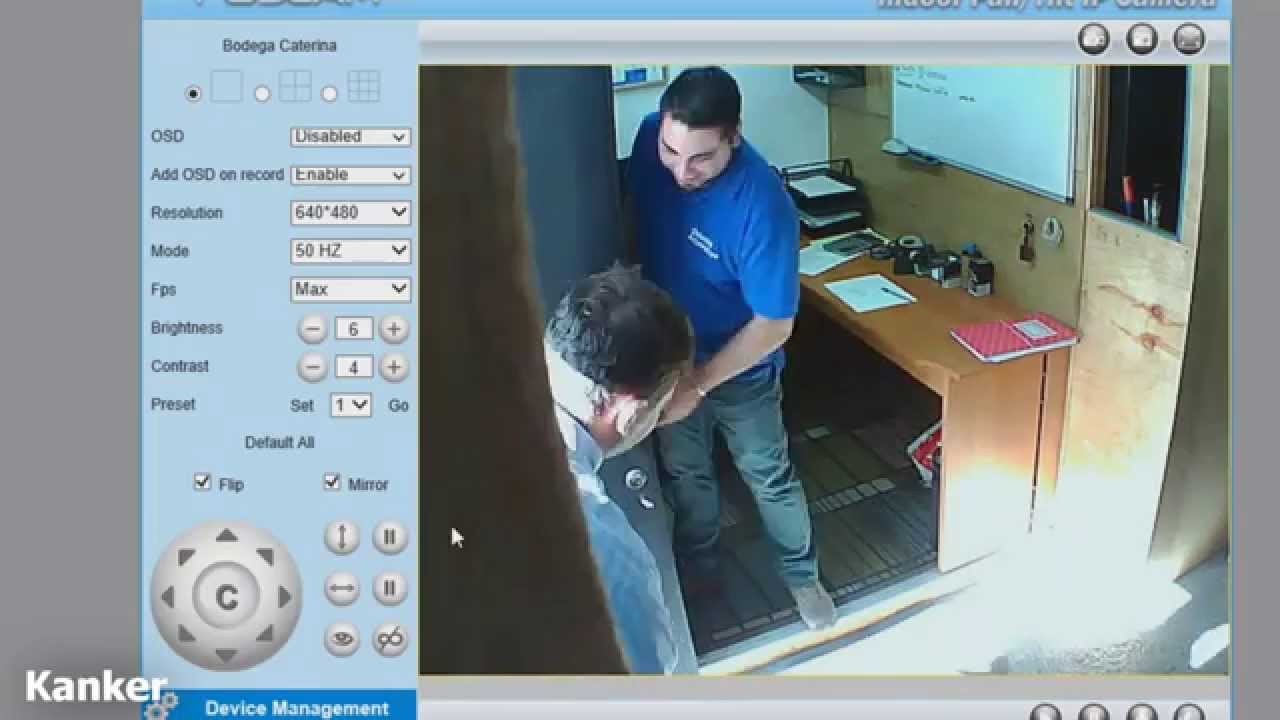
The digital landscape, once envisioned as a bastion of free information and secure communication, has unfortunately become a hunting ground for those seeking to exploit vulnerabilities. The intersection of readily available technology, a lack of robust security measures, and the anonymity afforded by platforms like Telegram has created a perfect storm for the exploitation of IP cameras. These devices, designed to provide peace of mind through remote monitoring, are increasingly being targeted and compromised, turning them into tools for voyeurism and, in the worst cases, facilitating criminal activity. The user base, often unaware of the risks, joins these groups and channels in the hope of accessing surveillance feeds, potentially exposing themselves and others to serious dangers.
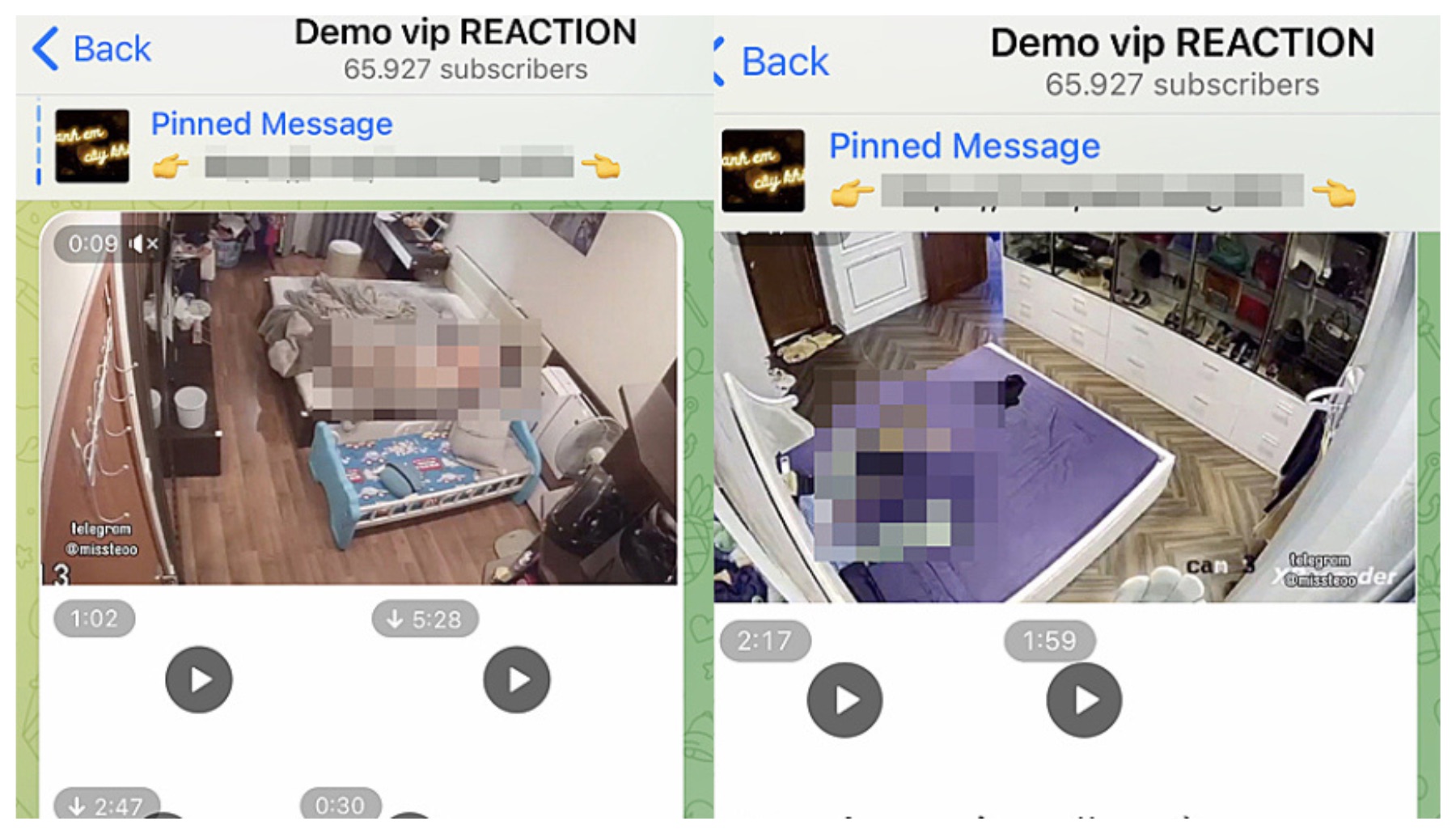
The ease with which one can join these channels and access the feeds is a disturbing aspect of this problem. Phrases like "If you have telegram, you can view and join" and calls to action like "You can view and join" are frequently used to entice users. These offers bypass any semblance of ethical considerations or legal compliance, and the groups often host content that ranges from breaches of privacy to the dissemination of illegal and harmful material. The availability of this content, as well as the ease with which users can discover it, poses a considerable threat to the vulnerable.
The following table presents a breakdown of the core elements involved in the compromised IP camera situation, providing clarity on the types of content, the platforms employed, and the underlying risks. This information is based on an aggregation of reports and observed trends within the digital environment.
| Category | Details |
|---|---|
| Targeted Devices | IP cameras of various brands and models; often those with default or easily guessable passwords. Hikvision cameras are explicitly mentioned as being vulnerable. |
| Content Shared | Live video feeds from compromised cameras. Examples include feeds from private residences, family homes, medical offices, and even strip clubs, as well as videos with disturbing contents. |
| Platform of Choice | Telegram. This platform's features, including large group sizes, end-to-end encryption for secret chats, and the ease of creating and joining channels, make it conducive to the spread of such content. |
| User Activity | Joining and participating in groups that share live feeds, seeking to access content without the consent of the owners of the cameras. |
| Risks involved | Privacy violation; potential for blackmail; potential for the distribution of illegal and exploitative content, including child sexual abuse material; and potential for enabling criminal activity due to the compromised security. |
The presence of such content is not simply a matter of technological curiosity; it also reflects deeply disturbing societal trends. The act of accessing private camera feeds without consent, regardless of the motivation, is a blatant violation of privacy. It is important to understand that this is not just a matter of innocent curiosity; it's a violation of trust. When a surveillance camera is installed, it is intended to provide a sense of security to those who are under its watch, not a vulnerability to others.
One of the main issues is the ease of access provided by platforms such as Telegram. As evidenced by the frequency of invitations to "view and join," the platform's infrastructure is designed to facilitate ease of access. It is easy to find, join, and share channels, which is problematic considering the nature of the content involved. Moreover, the anonymity and potential for rapid content distribution make it hard to contain the spread of compromised footage.
The use of Telegram bots to collect video feeds from IP cameras further exacerbates the problem. "This is a telegram bot that fetches a live record from an ip camera using rtsp protocol, motivated by me going on trips and wanting to keep an eye on my cats." This represents a shift, as the ability to collect and view feeds is now automated. The ease with which a user can set up these systems raises significant concerns about their widespread adoption and potential for abuse.
The motives behind these actions are varied. Some individuals may be driven by morbid curiosity or a desire for voyeuristic pleasure. Others might be motivated by a desire to exploit vulnerable individuals, potentially for financial gain through blackmail or other means. Regardless of the reason, the consequences are severe.
The potential for the exploitation of children is also a critical concern. The phrase "Hikvision cameras hacked, feeds sold as child porn" illustrates the possibility that these compromised camera feeds are being exploited for illegal activities. The sale of content, whether of adults or children, constitutes a serious criminal offence with a grave impact on victims, as well as the safety of the greater population.
Another dimension to this problem is the technical complexity of how these camera feeds are accessed. In many cases, vulnerabilities exist because the security practices of the camera owners are poor. Using default passwords, failing to update firmware, and not correctly configuring network security are common security vulnerabilities. Because the cameras are directly connected to the internet, they can be accessed remotely by anyone with the correct credentials.
Consider the case of a router's IP address changing. "If the router's ip address stays constant, we could stop right now and the ip cam project finished. However, the ip address is assigned by the isp and does not stay the same. We need a way to communicate the most current ip address. The usual way to do this is to get a domain name, and use a dynamic domain name service (ddns) to keep the ip." This illustrates the type of technical skill that is used for accessing and controlling the camera feeds, and also the technical knowledge needed to maintain the access.
The problem of hacked IP cameras is not simply a technological problem; it's a social and ethical problem. The creation and exchange of this kind of content indicate a significant erosion of privacy and respect for others. It demands that individuals take steps to protect their personal data and digital devices and that platforms assume greater accountability for the content hosted on their systems.
There is a pressing need for a multifaceted response that encompasses several crucial areas to combat this rising issue:
- Enhanced User Awareness and Education: A robust public education campaign is crucial. This campaign should emphasize the risks associated with joining unofficial Telegram channels and groups related to IP cameras, focusing on the potential for privacy breaches, the circulation of illegal material, and other related risks.
- Strengthened Device Security Protocols: Consumers must adopt and utilize robust security practices. This should include, but not be limited to, the consistent use of strong, unique passwords on all IP cameras, as well as other connected devices. Additionally, a focus on frequently updating firmware to patch security vulnerabilities is extremely important, as is configuring network security settings such as firewalls.
- Platform Accountability and Content Moderation: Platforms like Telegram need to be held accountable for the content hosted on their servers. This requires a proactive approach to content moderation, using advanced algorithms to detect and eliminate content relating to hacked IP cameras and any illegal content.
- Law Enforcement and Legal Action: The authorities need to actively investigate and prosecute those involved in the hacking of IP cameras and the dissemination of illicit content. This includes people who create the content, those who distribute it, and those who view and profit from it. It also requires strict legal frameworks that consider the seriousness of the crime and provide appropriate punishments.
- Collaboration and Information Sharing: Collaboration between technology companies, law enforcement agencies, and cybersecurity researchers is key. This collaboration must be focused on sharing threat intelligence, identifying vulnerabilities, and developing effective strategies to disrupt these activities.
By implementing these steps, a safer, more secure digital environment can be built, in which privacy is respected and the exploitation of vulnerable individuals is significantly decreased. This is not simply a technical challenge; it's a social responsibility that demands a coordinated and multifaceted strategy.
The use of the Telegram app and the invitation "Send message via telegram app" further underscores the integration of these platforms. This highlights the need for users to understand the specific risks related to the Telegram app as it relates to IP cameras. The privacy settings and the potential for third-party access should be thoroughly reviewed.