AWS IoT Secure Tunneling: Quick & Manual Setup Guide
Are you grappling with the challenge of securely accessing and managing your remote devices? The world of IoT is rapidly evolving, and with it, the need for robust and secure remote access solutions has never been greater.
The landscape of IoT device management is complex, but the core principle remains the same: enabling seamless and secure interaction with devices, regardless of their location. Traditionally, this has often involved cumbersome methods, such as sending control messages through MQTT topics or updating device shadows. These methods, while functional, can be challenging to implement and maintain, particularly when considering security and scalability.
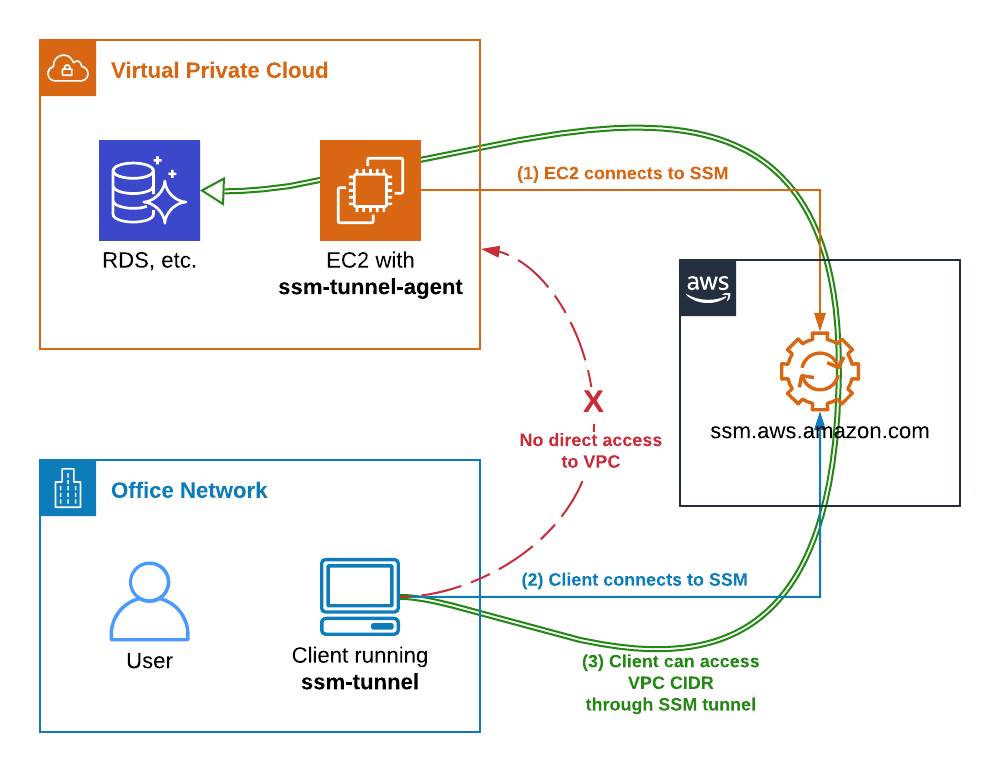
This is where AWS IoT Secure Tunneling enters the picture, offering a streamlined and secure solution for remote device access. It simplifies the process of establishing bidirectional communication to your remote devices, all within the secure embrace of AWS IoT's managed infrastructure. With Secure Tunneling, you dont need to wrestle with inbound firewall rules, maintaining the same level of security you've already established.
One of the key strengths of AWS IoT Secure Tunneling is its flexibility. You have the choice of quick setup or a more detailed manual setup, depending on your specific needs. This gives you granular control over configurations, allowing you to tailor the tunnel to your exact requirements. And, when you're ready to create a tunnel, the AWS IoT console provides a straightforward interface, whether you're starting from the tunnels hub or the details page of an existing IoT thing.
For those eager to explore the practical application of this technology, AWS provides comprehensive resources. Detailed tutorials guide you through the process, ensuring that you can quickly get up and running. Whether you're connecting to your device via SSH or exploring other services, AWS IoT Secure Tunneling provides a secure and efficient pathway.
The core of AWS IoT Secure Tunneling lies in its ability to create a secure connection. The service leverages the power of AWS IoT to manage and maintain a secure tunnel between your source and destination devices. This secure connection removes the need for frequent firewall adjustments, while still maintaining a high level of security. Using the Quick Setup method, for instance, allows you to quickly set up a new tunnel with default, yet editable configurations.
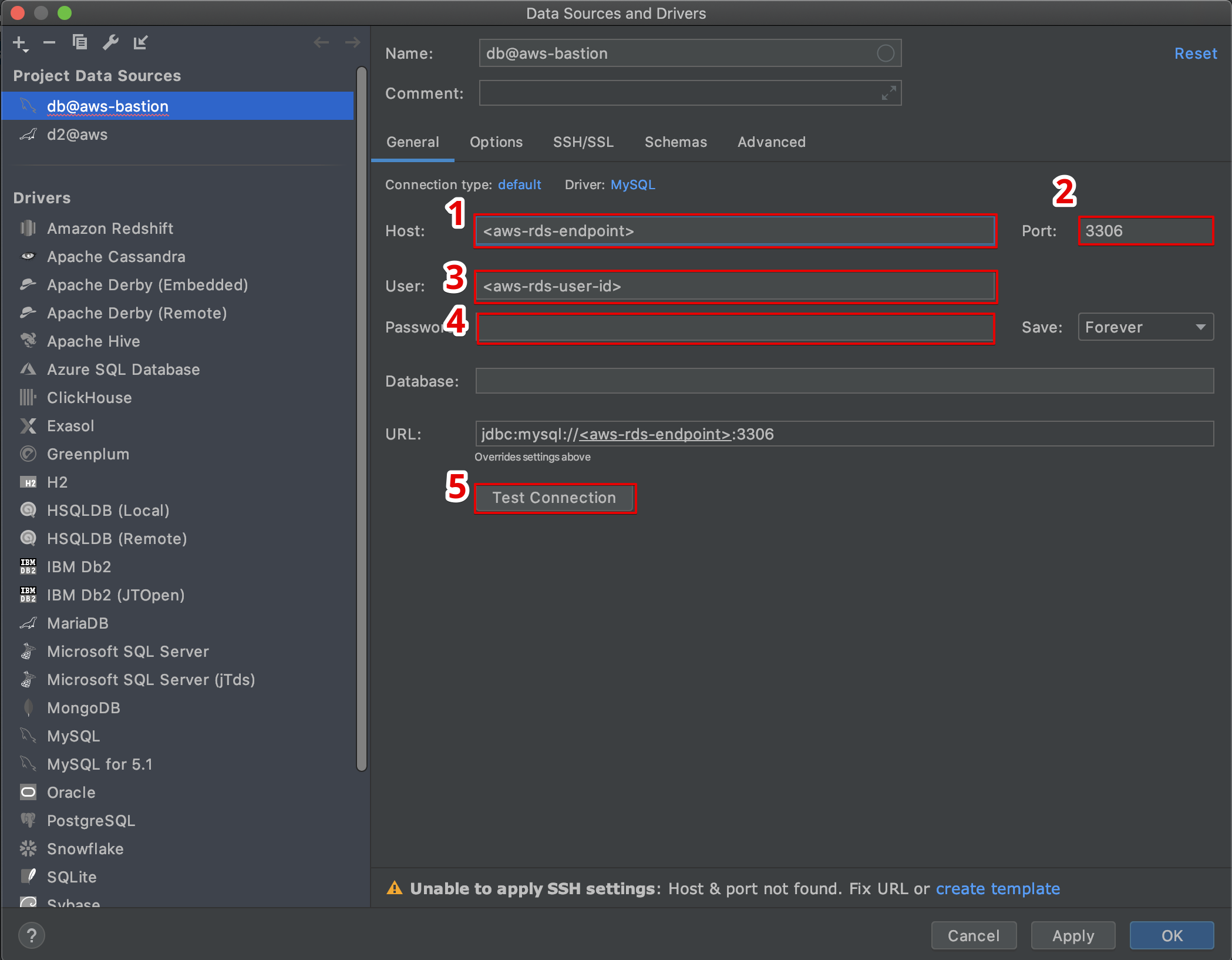
The service further simplifies remote access by only allowing SSH as the destination service. The access tokens are received after creating the tunnel using IoT Core, which are used for both source and destination. An important aspect of setting up your secure tunnel is defining a timeout for your credentials. It is generally recommended to keep the timeout low so that any potential token leaks are mitigated by their natural expiry.
One key advantage of this method is the ability to access devices from a web browser using secure tunneling. This is a boon for those looking to easily manage remote devices, and is made easy with the quick setup method. With the quick setup, it allows you to easily access the access tokens and SSH routing into your remote devices within a web browser.
Understanding the various aspects of secure tunneling, from initial setup to advanced configurations, is crucial for successful deployment. Whether you're a seasoned IoT developer or just starting, AWS IoT Secure Tunneling empowers you to build robust and secure remote access solutions.
The service also provides options for managing your tunnels. From the AWS IoT console, you can delete individual or multiple tunnels, easily cleaning up your environment as needed. For those preferring a programmatic approach, the AWS IoT API Reference offers API operations for deleting tunnels. This flexibility allows you to manage your tunnels in a manner that suits your workflow.
The entire process is designed with security at its core, using AWS IoT to manage the secure tunnel. This protects your devices and data, giving you peace of mind. With AWS IoT Secure Tunneling, you can access your devices without having to modify your existing firewall rules, thereby avoiding the complexities of constantly updating and managing those rules.
AWS IoT device management offers a wide range of tools that can be used by businesses to build IoT applications across all industries. This includes AWS IoT Secure Tunneling, which provides customers a way to establish bidirectional communication with remote devices using secure connections that are managed by AWS IoT. The benefits of using secure tunneling includes a reduction of the need to update your inbound firewall rule and helps keep the same security level provided by firewall rules.
AWS IoT Secure Tunneling is a key part of the broader AWS IoT Device Management suite. It helps establish secure, bidirectional communication with your remote devices over a secure, AWS IoT-managed connection. This simplifies remote access and enhances security, enabling businesses of all sizes to leverage the power of the cloud.